On October 4, Bloomberg Businessweek released an in-depth report detailing China’s cyber infiltration of nearly 30 U.S. companies utilizing microchips “as small as a sharpened pencil tip.” The report claims a unit of the People’s Liberation Army (PLA) was tasked with creating a microchip to be covertly inserted into server motherboards during manufacturing at Chinese factories for Super Micro Computer Inc., or Supermicro, one of the biggest sellers of server motherboards in the world. The tiny chips, which resembled signal conditioning couplers, incorporated memory, networking capability, and sufficient processing power for an attack. According to the report, when a compromised server was turned on, “the microchip altered the operating system’s core so it could accept modifications. The chip could also contact computers controlled by the attackers in search of further instructions and code.”
According to Bloomberg’s sources, Amazon Web Services ordered a third-party security audit into Elemental Technologies, a startup Amazon was hoping to acquire. Scrutiny of servers from Elemental revealed a microchip on server motherboards that were not part of the original design. Those servers were supplied by Supermicro. Also in 2015, strange network activity and firmware issues reportedly alerted Apple to a problem, leading to the discovery of these chips inside Supermicro servers in mid-2015. According to Bloomberg, Apple reported the incident to the FBI. The report claims investigators found the microchips may have affected almost 30 companies, including government contractors and a major bank, in addition to Amazon and Apple.
The Bloomberg article provides a hypothetical example of how these chips could compromise hardware: “Somewhere in the Linux operating system, which runs in many servers, is code that authorizes a user by verifying a typed password against a stored encrypted one. An implanted chip can alter part of that code so the server won’t check for a password—and presto! A secure machine is open to any and all users.”
The microchips could also steal encryption keys for secure communications, block security updates, and open new pathways to the internet. Any anomalies caused by the chips’ unusual activity might easily be dismissed by network administrators as unexplained but unimportant oddities. No companies or government agencies have confirmed Bloomberg’s report. Amazon, Apple, Supermicro, and the Chinese government all released statements refuting the explosive story. Apple maintains it has “never found malicious chips, “hardware manipulations” or vulnerabilities purposely planted in any server,” and never contacted the FBI about this type of incident. Supermicro insists it is “not aware of any investigation regarding this topic.” The National Security Agency (NSA), the U.S. Department of Homeland Security (DHS), and the UK’s national cyber security agency (GCHQ) do not currently doubt the companies’ rebuttals to Bloomberg’s claims.
On October 9, Senators Richard Blumenthal and Marco Rubio sent a letter to Supermicro, seeking answers to the allegations. Even Russia had to get a word in: Perhaps in an attempt to further cloud the distinction between media and “fake news,” Sputnik released an article entitled, “Report on Chinese Spy Chips Untrue, Demonstrates Shaky Journalism.”
Bloomberg doubled down on the supply chain threat from China, reporting new evidence on October 9 that a major American telecommunications company removed manipulated hardware from its network in August. Although the manipulation was different, it also was designed to give unauthorized individuals access to computer network data stored on the effected server. Furthermore, the alterations occurred as the motherboard was being manufactured–by a Supermicro subcontractor in China.
The veracity of these stunning reports by Bloomberg remain in question. Yet, regardless of whether or not events unfolded as Bloomberg reported, the critical lesson of the day is that the vulnerabilities are real. Jake Williams, former NSA hacker and founder of Rendition Infosec, told TechCrunch that even if the story “turns out to be untrue, the capability exists, and you need to architect your networks to detect this.” Chinese cyber and economic espionage is a large and growing threat for the United States. Less than a week after Bloomberg’s story broke, the New York Times reported that Belgium extradited a Chinese intelligence officer to the United States to face trial for economic espionage, allegedly stealing trade secrets from GE Aviation and other companies.
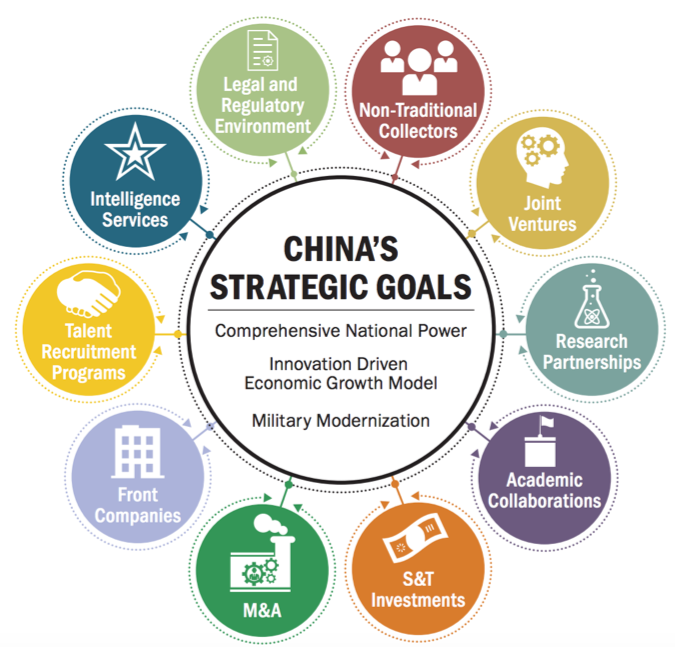
The National Counterintelligence and Security Center’s (NCSC) 2018 Foreign Economic Espionage in Cyberspace report named China, Russia, and Iran as some of the most capable perpetrators of economic espionage against the United States, especially in the cyber realm. China’s whole-of-government approach (outlined in the NCSC graphic below) to economic espionage and use of thousands of non-traditional collectors makes it especially effective. China has expansive efforts in place to acquire U.S. technology, including sensitive trade secrets and proprietary information, but the threat is not limited to China.
Numerous countries engage in economic espionage, even U.S. allies such as France and Israel. In today’s digital world, we often focus on hacking or phishing as cyberespionage methods, which, of course, are real threats. However, it can be easy to forget about other means for information theft. As Bloomberg’s article reminds us, physical and hardware intrusions remain a critical threat, both throughout the supply chain and once installed. Non-traditional collection techniques directed by foreign governments or enabled by disgruntled employees remain critical threats. Foreign economic and industrial espionage against the United States remains a “significant threat to America’s prosperity, security, and competitive advantage,” and no company is immune. American companies must continue investing in robust cybersecurity and counterintelligence structures to counter this still growing threat.






