2020 was already anticipated to be a year of tribulation as the nation prepared for what would inevitably be a contentious election. Add in COVID, civil unrest, continued social media dissension campaigns from internal and external actors, and overall unparalleled stress on the nation, our upcoming election is coming at a time when our country seems to be at a boiling point. Voting in a free and fair election is the most basic civil right, one on which many of the other rights of the American people depend. However, this fundamental element of our democratic process is under stress as never before. As we anticipate the unrest, conflict, and crises that will span pre-, during, and post-November 3rd, 2020, Concentric Advisors is identifying primary threats or areas of concern and possible trigger points that we will be monitoring closely to best prepare our clients, ourselves, and our nation.
Timeline
- November 3rd: Election Night
- As described below, results are not anticipated on Election Day
- December 8th: Deadline for states to resolve any disputes over the vote aka “Safe Harbor Deadline”
- December 14th: Electoral College votes
- January 6th: Congress tallies the Electoral College votes in a joint session led by the incumbent Vice President, Mike Pence
- Under the constitution, Congress has responsibility for counting Electoral College votes.
- January 20th, 2021: Inauguration Day; expiration of President’s term
- In the event no president is chosen (via a tie in the Electoral College), an acting president would serve as caretaker. This would be Nancy Pelosi as the Speaker of the House, if she retains her position in the new Congress. However, if both parties claim that their candidate is the winner, Pelosi could not step in.
- In any continuity of government scenario, whether due to COVID impacts or refusal to concede, there is an established Constitutional process. That process just may not be streamlined, initially obvious, nor without perceived meddling.
Unique Factors for 2020
Mail-In Ballots
As COVID continues and the preference to conduct personal business virtually remains strong with voters, the demand for mail-in voting is at an all-time high. The CDC has recommended voting via mail-in ballot in order to prevent exposure to COVID-19. Election Officials are bracing for half of all voters to do so by mail (up from 25% in 2016). As a result of the emphasis on mail-in voting, the services of the USPS are at a critical level as ballots are mailed and need to be received by election day in most states (some states allow votes postmarked by election day to be counted ex post facto).

Historically, there is a “blue shift” phenomenon observed by academics in recent elections where in-person-vote totals have tended to skew Republican, and absentee votes have leaned Democratic. As a result of the partisan opinions on mail in versus in-person voting, that blue shift is likely to be pronounced for the 2020 election. In July, the USPS sent a letter to states warning that some of their voting timelines were “incongruous with the Postal Service’s delivery standards”. The dependence on the USPS parallels ongoing disputes between the Trump Administration, Congress, and the USPS on procedures and funding. While the House of Representatives passed a $25B emergency grant for the USPS in mid-August in an attempt to counter any inefficiencies, the prevailing doubt in the ability of the USPS to deliver voters’ decisions on time is prevalent.
The legitimacy of mail-in voting has been recently called in to question. However, numerous nationwide and state-level studies over the years have not revealed evidence of major, widespread fraud. The rate of voting fraud overall in the US is between 0.00004% and 0.0009%, according to a 2017 study by the Brennan Center for Justice. Safeguards to ensure the authenticity of mail-in ballots include ensuring ballots match registered voters’ address and requiring signatures on envelopes, some even require witness or notarized signatures. Additionally, only valid voters received ballots in the mail, either through requesting or based on previous voter registration. The design of ballots also deters fraud through exact page size, color, and thickness varying by state or even county as well as varying methods of marking a choice and specific envelopes with unique bar codes. Ultimately with the punishment of voter fraud being five years in prison and a $10,000 fine, the “single extra vote is simply not worth the price” as stated by the Brennen Center for Justice.
Delayed Counting
As a result of the anticipated high volume of mailed in votes and the differing standards from each state, counts may not be tallied until at least 3 days after Election Day, even without any disputes or recounts. Additionally, voters are anticipated to come out in historic numbers, adding to the burden of election counters. In an environment where citizens are used to – and anticipate – immediate feedback on Election Day, this explainable delay may add fervor to the perception of nefariousness and allow for a greater window of insecurity prior to the official results. The FBI warned that the days after the election could result in “disinformation that includes reports of voter suppression, cyberattacks targeting election infrastructure, voter or ballot fraud, and other problems intended to convince the public of the elections’ illegitimacy”. This topic was even the closing remark at the first Presidential Debate on September 29th where the moderator, Chris Wallace, impressed on both party leaders to urge their supporters to remain calm during the anticipated extended period of ballot counting.
Refusal to Concede
Contentious election results are not an anomaly. Most recent in Americans’ mind is the Gore/Bush election in 2000 when the results came down to the infamous “hanging chads” in Florida and were only determined three weeks after Election Day after the case went to the Supreme Court. However, there have been at least three other times when election results were contested (1876, 1888, and 1960). Ultimately, each election result required, and resulted in, one party conceding. But what happens if both parties claim victory? Social media outlets have already predicated that they will add cautionary posts where campaigns or candidates prematurely claim victory.
On September 24th, President Trump stated “we’ll have to see what happens” in response to being asked if he would commit to a peaceful transfer of power. The inference that he may refuse to concede and could contest election results has resulted in a storm of activity from both sides of the political arena and the military, as well. Pentagon leadership has insisted the U.S. military has no role to play in any election dispute. “I, along with the entire U.S. military, will follow the lawful orders of the legitimate president of the United States as determined by law,” said Gen. Milley (Chairman of the Joint Chief of Staff), adding U.S. law stipulated there could only be one lawful president at a time. For reference, however, the Insurrection Act from 1807 does authorize the President to call in the armed forces to enforce laws and quell civil unrest.
Key Threat Drivers and Options for Risk Mitigation
Foreign Actor Meddling and Disinformation
As illustrated by the 2016 election, nation state meddling is most likely to take the form of spreading divisiveness and disinformation, mainly through online social media bots and troll farms utilizing “social cleavages”. Social cleavages include ethnic, religious, linguistic and regional divides and open vulnerability to conflict through manipulative identity politics. However, we increasingly see this tactic used within our own borders and by politicians on both sides of the aisle. By exacerbating existing social discord, actors can conduct an untraceable campaign of influence. Once enough followers engage, reshare, or amplify the messaging, the mainstream media can – and does – pick it up to only further broaden the reach of the message to new audiences. These campaigns can targeted in broad strokes to reach any voter, but they can also be customized to impact the state or even district level.
While “Russian interference” has maintained its status as an election buzz phrase since the 2016 elections, the Robert Mueller investigation reported that Russia did not directly change votes during the 2016 election; their meddling consisted of hacking and the spread of disinformation. Russia’s efforts led to the two-year Mueller investigation that cost an estimated $32-35 million (according to Time Magazine) and continues to sow distrust in the election process. Dan Coates, Director of the Office of National Intelligence, stated in January of 2019, “We assess that foreign actors will view the 2020 U.S. elections as an opportunity to advance their interests”. We can anticipate threats from not only Russia, but China, North Korea, and Iran, who are all advancing their cyber-capabilities. This meddling has previously been observed in hacking attempts, misinformation campaigns, exaggerated existing divisiveness, and overtly supporting one candidate over the other.

Targeted misinformation campaigns also serve to amplify discord. In recent years, the influence of conspiracy theorist groups such as QAnon have directly resulted in targeted acts of violence, such as when Edgar Welch fired shots inside a Washington pizzeria, believing the QAnon conspiracy that children were being held as sex slaves by politicians. Unfounded conspiracies have continued to spread rapidly and targeted parties increasingly must act to counter the messaging. One such example emerged earlier this year when the online retailer Wayfair was the subject of a conspiracy claiming that the company was selling children via female-named furniture advertisements. The conspiracy forced Wayfair to issue a statement explaining that they are not, in fact, trafficking children through furniture. The speed and efficiency with which conspiracy theories gain traction is a significant threat to the elections as the timing and pervasiveness of a theory could directly sway voters.
In recent months, Twitter and Facebook have begun providing “trust indicators” on posts in order to better inform the public. The effort was initially launched in March to ensure accurate information about the Coronavirus was being disseminated, however, the program quickly expanded to flag abusive behavior, manipulated media, misleading claims, glorifying violence, or fact checks for the consumers. While some welcome the effort, others view it as an infringement on the Constitutional right to free speech. Additionally, many companies in the tech industry have been accused of manipulating search results and suppressing conservative voices. These accusations, coupled with the recent trust indicator efforts, and the renewed effort to eliminate fraudulent accounts on Twitter, Facebook, and Instagram, combine for a perception of influencing the political debate.
Mitigation: While you can’t prevent you or your company’s name from being included in the latest conspiracy theory, you can mitigate its effects by making sure you are constantly searching both the deep and dark webs for any inaugural threats. Threats outside of the conspiracy realm need consideration, as well. Updates on ongoing protests, indications of violence, or abnormal attention surrounding your business or home should all be monitored and taken seriously for their potential impact to your business and the safety of yourself and your employees. Outside of monitoring, ensure your company has an updated crisis management and communications plan and has conducted a Red Team analysis in order to develop contingencies and preplanned responses.
Civil Unrest/Physical Security
Throughout 2020, multiple important social initiatives have resulted civil unrest and international protests, even during the prioritization of social distancing due to COVID. It seems weekly current events and announcements continue to amplify the divisiveness across the country resulting in protestors and counter-protestor intellectual or physical clashes. Election results will inevitably stoke this fire, regardless of outcome. Known domestic terrorists such as QAnon or the white supremacist hate group “Proud Boys” were both officially watch listed by the FBI. Facebook has stated that it will “restrict the circulation of content” on its platform if the election descends into chaos or civic unrest.
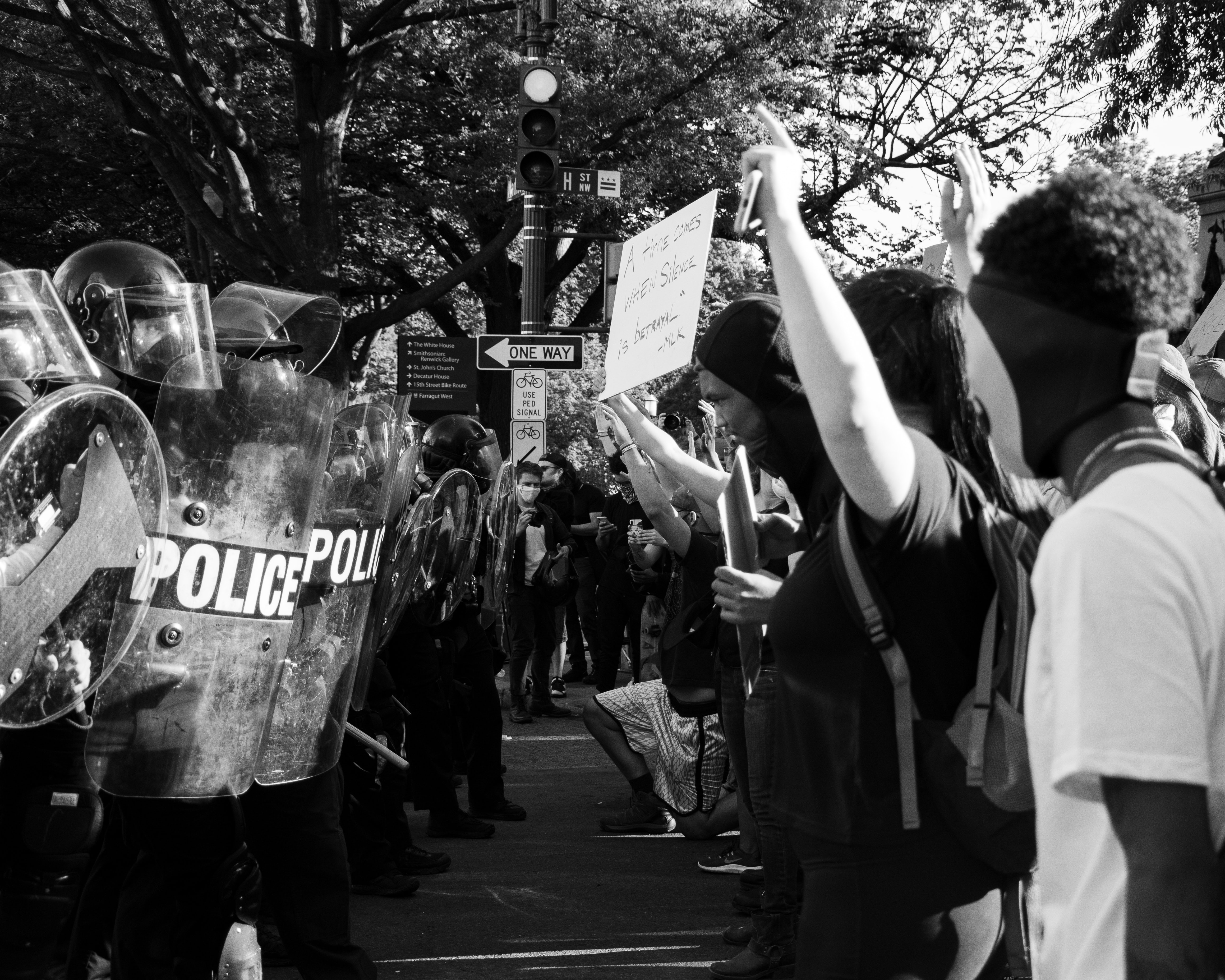
The idea of attacks on election venues conjures up images seen in Afghanistan or Libya, however, the strategic effect of targeting basic voting rights is an international phenomenon. Any number of groups could utilize attacks on physical infrastructure to disrupt, discredit, or derail an election. The perceived inability of our government to protect citizens’ right to vote safely would contribute to the overall undermining of election security. More than 230,000 polling places were used in the 2018 general election; the sheer amount makes physical security, for which the state is responsible, nearly impossible. Security officials will depend on online indicators to predict which polling locations may be the target of a physical attack. However, polling stations are not the only physical security concern: according to the U.S. Agency for International Development (USAID), physical security concerns during elections include facilities, materials, offices, polling stations, media organizations, and residences of political figures.
The requirement and request for “poll watchers” is not unique to 2020. Most states allow political parties and campaigns to appoint people to sit inside polling sites to monitor voting. However, those appointed personnel must adhere to the rules including addressing any concerns with the chief-on site election official; they are strictly prohibited from interacting with the voters directly. The self-appointed poll watchers are security officials primary concern due to potential intimidation and deterrence of voters. Previous calls for masses of self-appointed poll watchers have not materialized before, but their presence during the 2020 election could amplify the already-heightened civil discord.
Mitigation: Outside of keeping abreast of current events that may impact your operating area, residence, or office, reviewing and updating physical security protocols and measures are crucial. Identify physical vulnerabilities and acquire mechanisms for identifying if those vulnerabilities are being breached. This preparation spans from a dedicated guard force during anticipated insecure events to activating virtual security services to more sensitive standards.
Fiscal Impact/Market Insecurity
As we have seen in recent months, the stock market has reflected the ongoing insecurity due to COVID and civil unrest. All three major U.S. stock markets indices bottomed out on March 23rd, when the number of confirmed COVID cases in the United States stood at 43,000 (we are now at over 7.19 million cases). Since then, the stock market has continued to fluctuate but has yet to return to “normal”, operating at only 79% of its pre-COVID level according to CNN business. The stress on the market runs counter to the norm during presidential election cycles, given that in 17 of the last 23 presidential election years, the market ended the year on a positive note (average annual return of 7.1%). While the old adage remains “the stock market is not the economy”, the extreme reactions seen since March only validate that volatility is not limited to emotional reactions and historical data can hardly predict the year of 2020 variables.
Mitigation: Anticipate volatility in response to the current events as well as an “abnormal” election year for stock market activity. Additionally, a lack of responsiveness from banks, investors, and government agencies can be expected as they conduct internal responses to the elections.
Cyber Security
“Cyber security” is a broad title for the possibility for cyber intrusion in a multitude of venues, including voter registration, breaching/stealing voter data, electronic poll books, or changing personal data all in order to cause confusion, frustration, and distrust within the system even without changing the actual vote. With standards for securing voting machines, specifically their connectivity to the internet, varying from state to state, actors could target vulnerable systems through either their internet connections or overall lack of cyber security. Any intrusion into the network that would require reverting to redundant or back up vote count methods (usually paper-based) would only prolong the results and exacerbate the cynicism surrounding the process. Cyber security experts call this a “perception hack”.

While we associate cyber security concerns primarily with voting on Election Day, registering to vote also provides a unique vulnerability. According to the May report from the Senate Intelligence Committee, Russia attempted to scan election systems in 21 states and aggressively attempted to infiltrate six of them, resulting in the theft of personal information for half a million voters. 2020’s anticipated increase in virtual registrations expands the opportunity for bad actors leading up to the Election Day.
Mitigation: Cyber security of the elections can propagate to the personal level with cyber actors taking advantage of “digital dust” to make companies and personnel vulnerable to doxing. To ensure your own personal cyber security, acquire services for scraping personal identifiable information (PII) from the open web and conduct audits of both personal and corporate online presence to identify any vulnerabilities. Regular monitoring can reduce the likelihood of fraudulent or malicious use of your exposed data.
Ultimately, we need to prepare ourselves for a drawn-out election decision due to the inevitable time delay that will result from counting mailed in ballots. The legitimacy of the election will ultimately be determined by the perception by important segments of society that the government is exercising state power in ways that are reasonably fair and in the interests of the nation as a whole. As subjective as that criteria is, especially in the charged environment we currently find ourselves, we need to be prepared for, while not prematurely default to, crisis.
Concentric Advisors is here to help you prepare for this upcoming period of insecurity
Stay tuned for our virtually hosted seminar where we discuss Election Insecurity with experts throughout the field
As we strive to provide insight for our clients and assist them through this most unusual election season, Concentric Advisors is hosting Roundtable planning sessions for leaders to explore these issues while also taking a critical look at their organizational resilience.
The Roundtable will include:
- Explanation of events after November 3 that will determine the election outcome
- Exploration of malign actors, including foreign governments and violent domestic groups
- Checklist of issues to address with supporting teams, such as resiliency and communications planning, potential relocation of executive leaders, and public pressure campaigns
- Checklist of steps to take regarding personal and family security
If you would like Concentric Advisors to facilitate a roundtable session for your organization, please contact Max Anderson at manderson@concentricadvisors.com for more information.
Resources:
- CISA: cisa.gov/protect2020
- DOJ/FBI: fbi.gov/investigate/counterintelligence/foreign-influence/protected-voices
- ODNI: dni.gov/electionsecurity
- All Sides Media Bias chart: https://www.allsides.com/media-bias/media-bias-ratings






